In the last few years, we’ve seen a disturbing trend—intruders are innovating much faster than defenders are. We’ve seen the “commercialization” of malware, with attack kits available at cheap price on underground forums for anyone who wants to plan a variety of attacks. Large botnets are available for rent, allowing attackers to send spam or launch DDoS attacks at will.
There is global acceptance that access to timely cyber threat intelligence is a critical defense strategy in our dynamic cyber threat landscape. Therefore, the motive behind cyber threat intelligence is to provide the ability to recognize and act upon indicators of attack and compromise scenarios in a timely manner.
But as per the recent surveys, the there’s a lot of confusion around what threat intelligence is and how it’s delivered and consumed.
Before selecting the sources, we need to find out the answers of the two most important questions:
• Will this information provide me with actionable intelligence that is relevant to my organization’s sector, region, and / or infrastructure?
• Will this information provide me with valuable information to build our long-term knowledge base and strategy?
Context is key
Only information with its associated context can be considered intelligence. Without that context, that information is merely data. While sourcing intelligence, it is important to ensure that the source includes the proper context along with its data. The context need not be complicated or fancy, but should provide enough instruction regarding how to use the intelligence operationally.
For example, “these domain names are command and control domain names” or “these URLs are drop sites” provide adequate context, while “here is a long list of IP addresses for which there is no additional context” does not. If the intelligence offering does not include that important contextual information, it is probably not really much of an intelligence offering.
How companies are doing this?
They are accepting and consolidating feeds through their security information and event management (SIEM) and intrusion monitoring platforms, while relying on CTI feeds from a variety of sources, including the security community and vendor-driven feeds from the various tools they are using to secure their networks, systems and data. The best key best practices are strong planning, leveraging internal systems and intelligence and defining gaps and workarounds contributing to successful CTI implementations.
Those who’ve adopted CTI report improvements in the following areas:
• Ability to see attacks in context
• Accuracy of detection and response
• Faster detection and response
What Is Cyber Threat Intelligence?
Gartner has defined threat intelligence as: “evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.”
Threat intelligence, also known as cyber threat intelligence (CTI), is organized, analyzed and refined information about potential or current attacks that threaten an organization.
Figure 1 displays the different stages of a typical attack pattern and responses leading back to actor actions. CTI can help organizations more readily identify delivery mechanisms, indicators of compromise across infrastructure, and potentially actors and specific motivators as well.
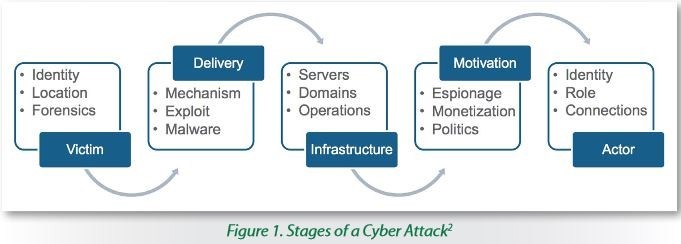
Cyberthreat intelligence, when used correctly, can help defenders detect attacks during—and ideally before—these stages by providing indicators of actions taken during every stage of the attack.
Cyber threat intelligence helps you to make better decisions about your defense and other benefits along:
Adopt a proactive approach instead of reactive; you can create the plan to fight against the current and future threats
• Adopt a proactive approach instead of reactive; you can create the plan to fight against the current and future threats.
• Organize the security alert mechanism, know before they attack you.
• Always provide the better response to the security incidents
• Use the cyber intelligence feeds to provide your security technologies up-to-date information to block the emerging threats
• Of course a better investment regarding risk and benefit analysis.
What are the indicators of attacks?
Some of the places defenders can detect these indicators of attack include logs, system reports and security alerts that can provide the following visibility:
• Account lockouts by asset and user
• All database access events (success/fail)
• Asset creation and deletion
• Configuration modifications to critical systems
• External activity to commonly hacked ports (1080, 135, 139, 1433, 21, 22, 23, 3306,3389, 445)
• Activity on honeypot assets or files
• Login and access logs
• Denial-of-service attacks
• IDS and/or IPS events
The actual indicators they look for in these and other systems include:
• Activity in accounts of former staff
• Activity on same asset with different user names (within short time period)
• Outside-of-hours logins to systems with critical data
• Outside-of-hours systems’ access by system and user
• Brute force logins
• Privileged accounts created or changed
• Remote email access from countries not typically involved in normal business operations
• Remote logins from countries not typically involved in normal business operations
• Repeated unsuccessful logins (administrative and user) by asset
• Systems accessed as root or administrator
• Traffic between test and development or live environments
• User logged in from two or more assets simultaneously
Cyber Threat Intelligence has following major categories:
1 .Commercial threat intelligence services
2. Open Source Threat Intelligence/frameworks
3. Cyber Threat Intelligence feeds
Let’s explore all the aforementioned categories:
Commercial threat intelligence services
The market-leading threat intelligence vendors and services
• Cyveillance Cyber Threat Center
• Dell SecureWorks
• FireEye Threat Intelligence
• Internet Identify (IID) ActiveTrust
• LogRhythm Security Intelligence
• RSA Live and RSA Security Analytics
• Symantec DeepSight Security Intelligence
• VeriSign iDefense
Open Source Threat Intelligence
• Open Threat Exchange (OTX)
• Structured Threat Information Expression (STIX)
• Collective Intelligence Framework (CIF)
• Open Indicators of Compromise (OpenIOC) framework
• Trusted Automated eXchange of Indicator Information (TAXII)
• Traffic Light Protocol (TLP)
• Cyber Observable eXpression (CybOX)
• Incident Object Description and Exchange Format (IODEF)
• Vocabulary for Event Recording and Incident Sharing (VERIS)
Cyber Threat Intelligence Feeds – Top list
• AlienVault.com: Multiple sources including large honeynets that profile adversaries.
• CrowdStrike.com: Advanced threat intel as part of their threat protection platform.
• Cyveilance.com: Unique feeds on threat actors: indications of criminal intent.
• EmergingThreats.net: A variety of feeds.
• FireEye.com: DTI- Dynamic Threat Intelligence service.
• HackSurfer.com (SurfWatch): Insights tailored to your business.
• HexisCyber.com: Feed supports automated actions.
• InternetIdentity.com: Threat feeds from their big data solution ActiveTrust.
• iSightPartners.com: ThreatScape series.
• LookingGlass.com: Maps of infrastructure, connectivity and ownership, plus threat intel.
• MalwareCheck.org: Intelligence on any URL
• MalwareDomains.com: A list of domains known to be associated with malware.
• RedSkyAlliance.com: A vetted team of corporate computer incident responders and security professionals.
• RecordedFuture.com: Organizes information from the Internet.
• SecureWorks.com: Provides feeds and also instruments networks.
• Symantec.com: DeepInsight feeds on a variety of topics including reputation.
• Team-Cymru.com: Threat intelligence plus bogon lists.
• TheCyberThreat: Twitter feed. High level but comprehensive and curated.
• ThreatConnect.com: by Cyber Squared. Focused on information sharing.
• ThreatGrid.com: Unified malware analysis. Now part of Cisco.
• ThreatIntelligenceReview.com: Updated reviews of threat intelligence sources.
• ThreatStop.com: Block Botnets by IP reputation.
• ThreatStream.com: Famous team. Multiple sources in interoperable platform.
• ThreatTrack.com: Stream of malicious URLs, IPs and malware/phishing related data.
• Verisigninc.com: iDefense feeds highly regarded by some key institutions.
References: sans.org, computerweekly.com, thecyberthreat.com, sagedatasecurity.com, searchsecurity.techtarget.com, esentire.com,infosecinstitute.com
Please share your thoughts and experience. Suggestions most welcome



